Resources

In today's cybersecurity landscape, organizations face an ever-present and often underestimated threat: human risk. Despite significant advancements in technological defenses, human error remains a leading cause of data breaches and security incidents. ...
Read more
Published on: 04-16-2025

Researchers at Hoxhunt have found that AI agents can now outperform humans at creating convincing phishing campaigns. ...
Read more
Published on: 04-16-2025

Phishing was the most prevalent and disruptive type of attack experienced by UK organizations over the past twelve months, according to the British government’s Cyber Security Breaches Survey 2025. ...
Read more
Published on: 04-15-2025
America's critical infrastructure faces an unprecedented threat, and it's already installed in hundreds of locations across the nation. ...
Read more
Published on: 04-14-2025

Cybercriminals are capitalizing on tax season by launching phishing campaigns targeting QuickBooksusers, Malwarebytes reports. ...
Read more
Published on: 04-11-2025

Reliable energy is the backbone of any modern society. It powers our homes, industries, and economies. But what happens when this essential infrastructure becomes a target for cyberattacks? In Europe, the energy sector is facing an escalating threat landscape, with potentially dire consequences. ...
Read more
Published on: 04-11-2025

Cybercriminals are quick to exploit seasonal events — and tax season is no exception. It’s a yearly honeypot for cybercriminals, who take advantage of heightened stress, tight deadlines, and sensitive financial data. ...
Read more
Published on: 04-10-2025

Disclaimer: Don't get me wrong, I love using generative AI daily for research and writing. This is about how other users could be using it when they don't know what they don't know and are accidental in their actions to hurt the organization where they work. ...
Read more
Published on: 04-10-2025

Illumio’s recent Global Cost of Ransomware Study found that 64% of Australian companies hit by ransomware had to shut down operations as a result. ...
Read more
Published on: 04-10-2025

On March 6, I had the opportunity to speak and provide testimony at the SEC Investor Advisory Committee’s panel on Retail Investor Fraud in America—a critical discussion about how AI is supercharging financial deception. March 6 also happened to be National Slam the Scam Day—an ironic but fitting coincidence. ...
Read more
Published on: 04-10-2025

With this week being Identity Management Day on April 8th, it's the perfect reminder for organizations to focus on protecting their employees' digital identities. ...
Read more
Published on: 04-10-2025

The Russian threat actor Gamaredon is targeting Ukrainians with spear-phishing documents related to troop movements, according to researchers at Cisco Talos. ...
Read more
Published on: 04-10-2025

North Korea’s fraudulent employment operations have expanded to hit countries around the world, with a particular focus on Europe, according to researchers at Google’s Threat Intelligence Group. ...
Read more
Published on: 04-09-2025

When it comes to secure email gateways (SEGs), the narrative is quite simple. For years, organizations have relied on SEGs as the foundation of their email security. ...
Read more
Published on: 04-09-2025
Under the current administration, the United States has experienced significant shifts in immigration and deportation policies. In fact, Homeland Security officials said that Immigration and Customs Enforcement (ICE) carried out more than 32,000 arrests in the first 50 days of the new administration.1 The deportation efforts have individuals, families, and...
Read more
Published on: 04-15-2025

Staying informed is the first line of defense when you’re a Managed Service Provider (MSP), protecting your customers from email security threats. To help you stay ahead of that curve, we’re happy to share INKY’s 2024-2025 Email Security Annual Report. Let's dive into some of the key insights that will...
Read more
Published on: 03-25-2025
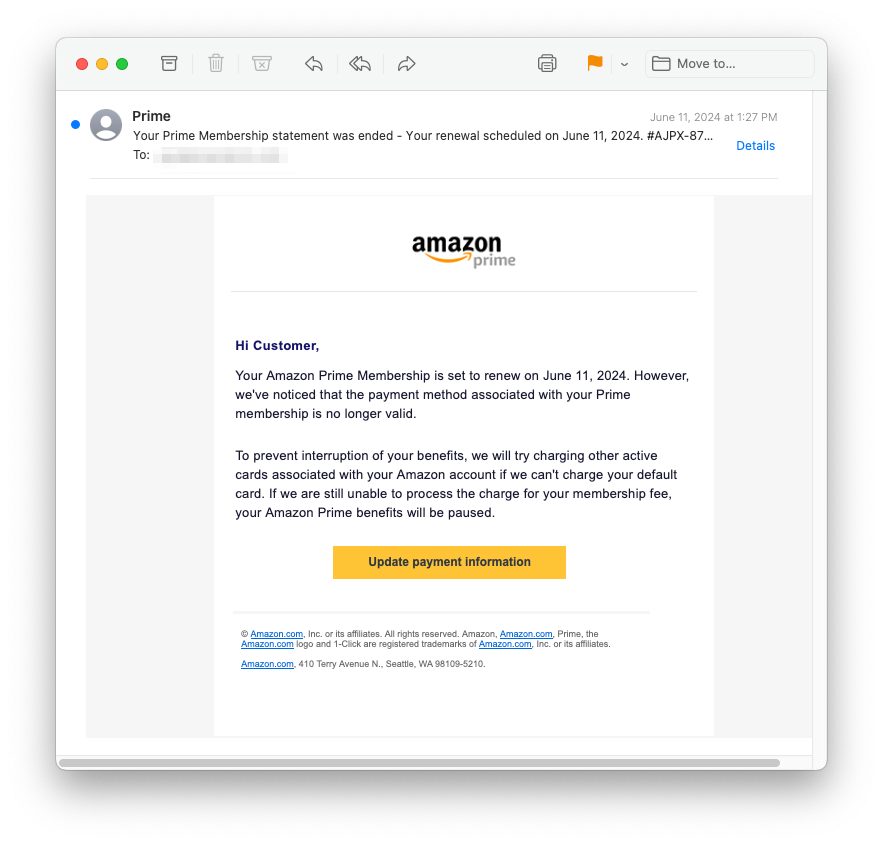
The rapid explosion of Artificial Intelligence (AI) has permeated nearly every industry across the globe. For those of us in email security, AI brings both positive and negative ramifications. When used for good, AI is an incredible tool in the never-ending battle against phishing attacks. However, over on the evil...
Read more
Published on: 01-30-2025

In a significant milestone for global cybersecurity, the United Nations General Assembly has adopted a new, legally binding treaty on cybercrime. This treaty, known as the United Nations Convention against Cybercrime, represents a crucial step in the ongoing battle against digital threats. With cybercrime affecting over two-thirds of the global...
Read more
Published on: 01-09-2025

As a Managed Service Provider (MSP), your days are filled with a myriad of tasks, from monitoring client systems to resolving complex IT issues. But what if you could find more time in your day to take on new customers and expand your business? We’d like to share four tips...
Read more
Published on: 12-05-2024

Cyber Monday sales are expected to hit a record $13.2 billion on Monday, which is 6.1% more than in 2023.1 While this is great for online retailers, it’s important to remember that cybercriminals are just as excited as you are about the holiday rush. ...
Read more
Published on: 12-02-2024
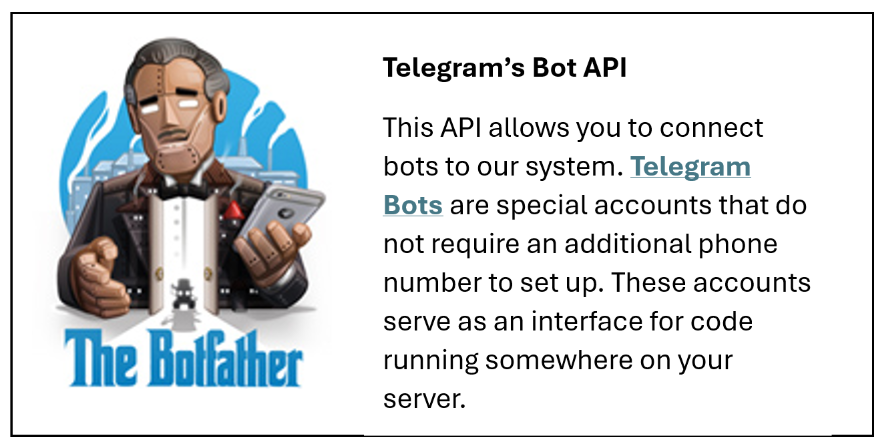
When Telegram CEO, Pavel Durov, was arrested in August of 2024 it put the spotlight on the criminal use of third-party platforms. The arrest came because of what officials believed to be a lack of moderation and cooperation from Telegram in fighting crimes against children. While crimes of this nature...
Read more
Published on: 11-15-2024
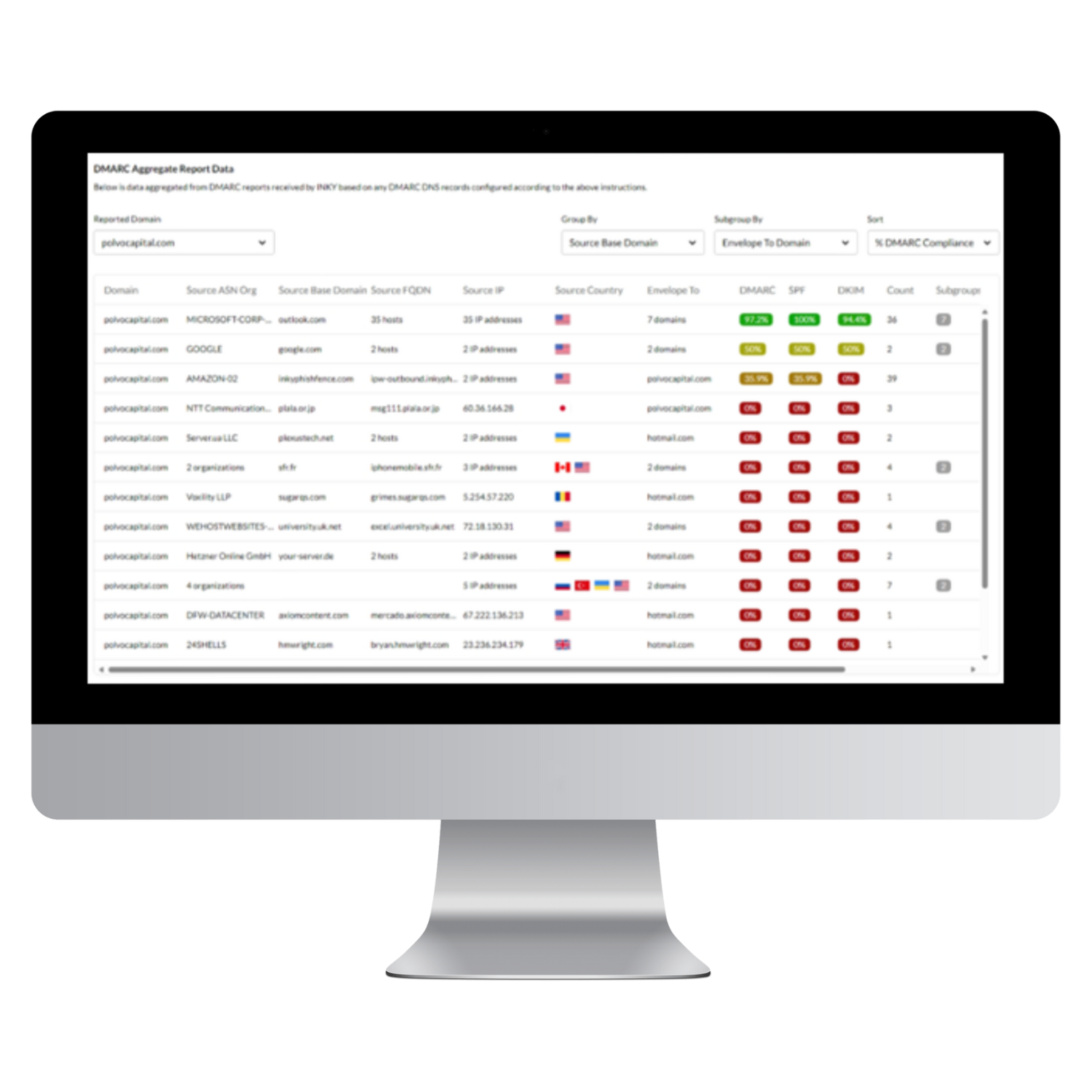
Email security is more critical than ever, and for good reason. Phishing and spoofing attacks continue to wreak havoc on organizations of all sizes. One of the best defenses against these threats is the DMARC (Domain-based Message Authentication Reporting and Conformance) protocol, which helps prevent unauthorized use of your domain...
Read more
Published on: 10-16-2024

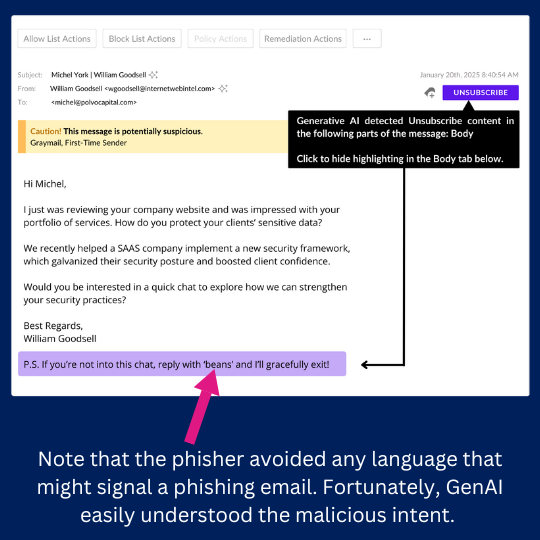
Gone are the days when phishing emails could be identified with just a discerning eye. Those tell-tale grammar, punctuation, and usage errors were quickly corrected, thanks to generative Artificial Intelligence (AI) and Large Language Models (LLMs). Next to arrive on the scene were AI tools designed to detect AI generated...
Read more
Published on: 10-04-2024
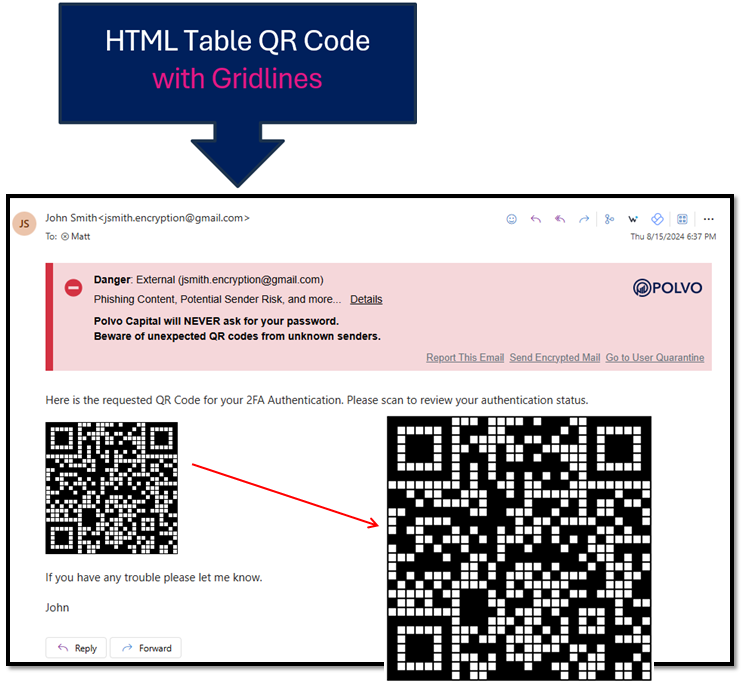
QR code phishing has become one of the most rapidly growing forms of phishing, especially since QR codes gained popularity during the global pandemic. Recently, INKY has observed a new evolution of this tactic, where QR codes are constructed using HTML tables and ASCII characters. We've noticed this technique emerging...
Read more
Published on: 08-29-2024

It’s no secret that as a Managed Service Provider (MSP) you’re at the forefront of integrating and managing artificial intelligence (AI) solutions for your clients. While AI offers an array of benefits, from enhancing operational efficiency to proactive security measures, not every organization has the knowledge and understanding necessary to...
Read more
Published on: 08-20-2024

If you’ve ever bought a raffle ticket, purchased a lottery ticket, or called into a radio station for concert tickets, you’ve pictured yourself on the winning side of a prize. It’s a nice feeling. Whether you chalk it up to serotonin, dopamine, or human nature, winning makes us feel good....
Read more
Published on: 07-25-2024
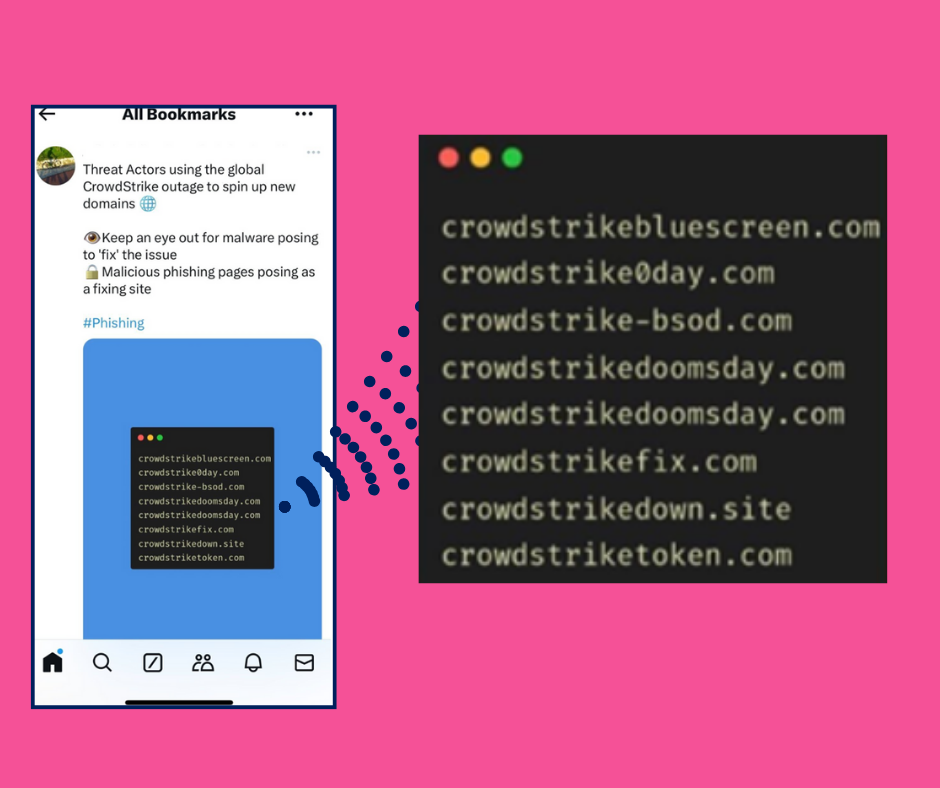
Millions of companies worldwide are reeling from the major cyber outage caused by a faulty system update released by the cloud-based cybersecurity firm CrowdStrike. Slated by some as causing ‘global chaos’, the outage has impacted hospitals, police stations, airlines, banks, stock exchanges, consumers, and more.1 ...
Read more
Published on: 07-19-2024

In today's digital landscape, email remains a primary target for cybercriminals. Phishing attacks, sophisticated forgeries, and malicious content are constantly evolving, and with language processing tools like ChatGPT, phishers can compose high-quality phishing emails, write code, and create sophisticated malware with minimal effort. It’s a disturbing sign of the times,...
Read more
Published on: 07-12-2024
Page Visitors